Securing Operators and Nation-states Critical Mobile Infrastructure
Rely on world renown OT security expertise to optimize the security of your mobile infrastructure.
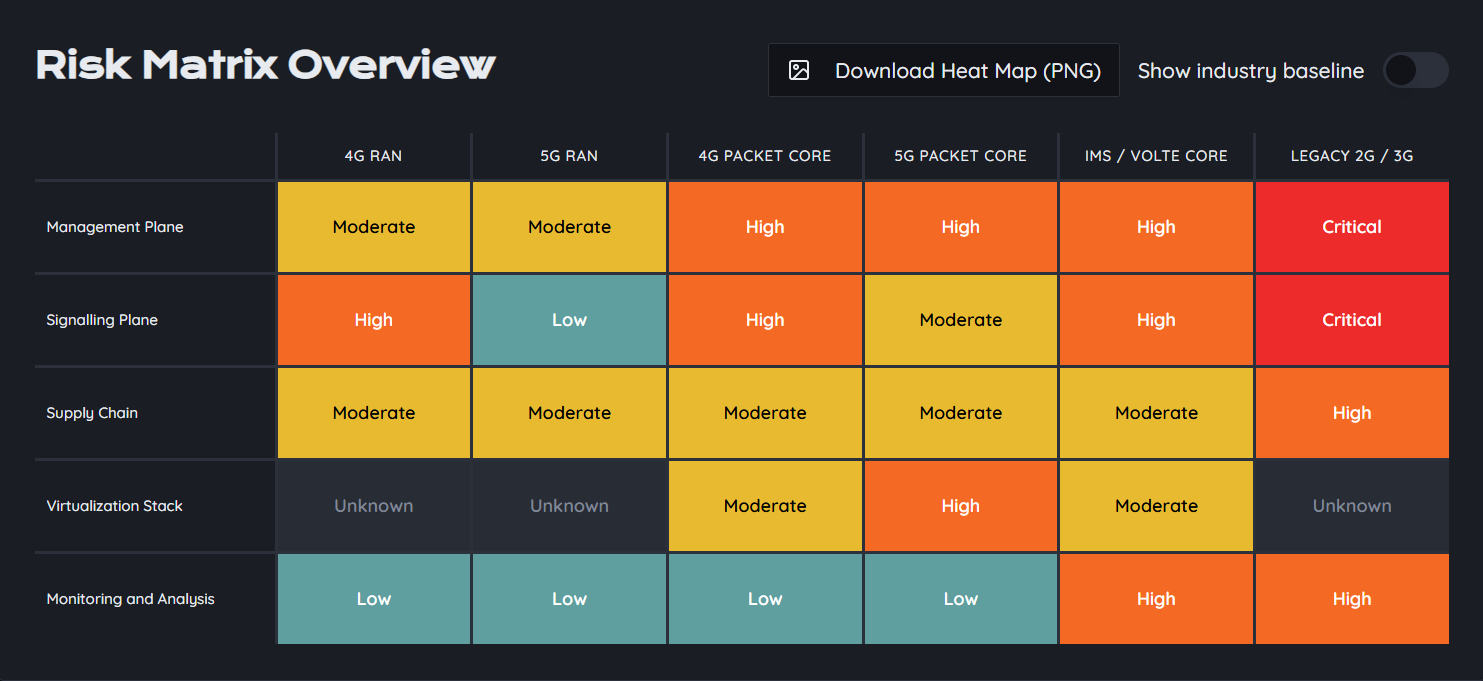
World leader in mobile network security
We help operators, governments and enterprises to defend against all network cybersecurity threats and attacks. Founded in 2009, P1 Security is one of the most trusted companies in network security with proven experience on all major technologies and network protocols.

Products and services dedicated to enhancing the level of safety on all major telecom protocols standards
Upscale your security stack
We provide software to automate the identification and detection of potential threats in your signalling protocols and help you remediate their consequences to provide increase security to your subscribers.
- ASM (PTA) - Attack Surface Management - Identify vulnerabilities on your network and get correction recommendation.
- IDS (PTM) - Intrusion Detection System - Detect malicious activity on your different protocols and take action to remediate the threat.
- VKB - Vulnerability Knowledge Base - Unique database of 2000+ telecom vulnerabilities from all protocols and major equipment vendors.

Surround yourself with specialists
Our experts have been advising the most critical infrastructure for almost 15 years on topics going from security audits to full security architecture review through vendor management
- Passion - We are a group of engineers truly fascinated by telecom security.
- Expertise - Our research, our missions, our trainings makes us as the top experts currently.
- Exhaustivity - With experts in all protocols or disciplines, we can cover your every needs.

Some example of P1 Security's intervention
We work throughout the world for some of the most demanding clients on the planet.
- Audit of the 5GCore equipments in a RFP for a new infrastructure deployment.
- NFVI Architecture Comparison for an top asian MNO before deciding on a route to 5G deployment.
- National signalling threat detection from several operators for a MEA government.

From legacy signalling protocols deployed for tens of millions to virtualized network functions in private environment
2G-3G SS7
Fortify your network with our specialized 2G-3G SS7 portfolio. Unparalleled expertise in securing signaling protocols for robust telecom defense.
4G LTE Diameter
Diameter is everywhere, 4G is actually 5G... And its risks need to be assessed and monitored to ensure better safety for everyone.
IMS, VoLTE, VoWIFI
Comprehensive IMS, VoLTE, VoWiFi solutions for telecom security. Elevate your network defense with our specialized expertise.
5G and Private 5G
Explore specialized solutions for 5G and Private 5G network security. Benefit from our expertise in defense.
LTE RAN / Ng RAN
The radio access network needs at least as much focus as the core, the radio or the UE.
Enterprise Security & Mobile
Enterprises need to get in the security conversation with their network service providers to ensure the safety of their stakeholders.
Infrastructure Security (NFV)
Network virtualization comes with as much risk as it comes with opportunities. Both are massive.








.jpg)