Attack Surface Management
Your security always depends from one single uknown and critical vulnerability: Identify what and where to fix in your Mobile & Telecom OT Networks. Prioritize each remediation task and verify network hardening. Scan and cover all your OT networks.

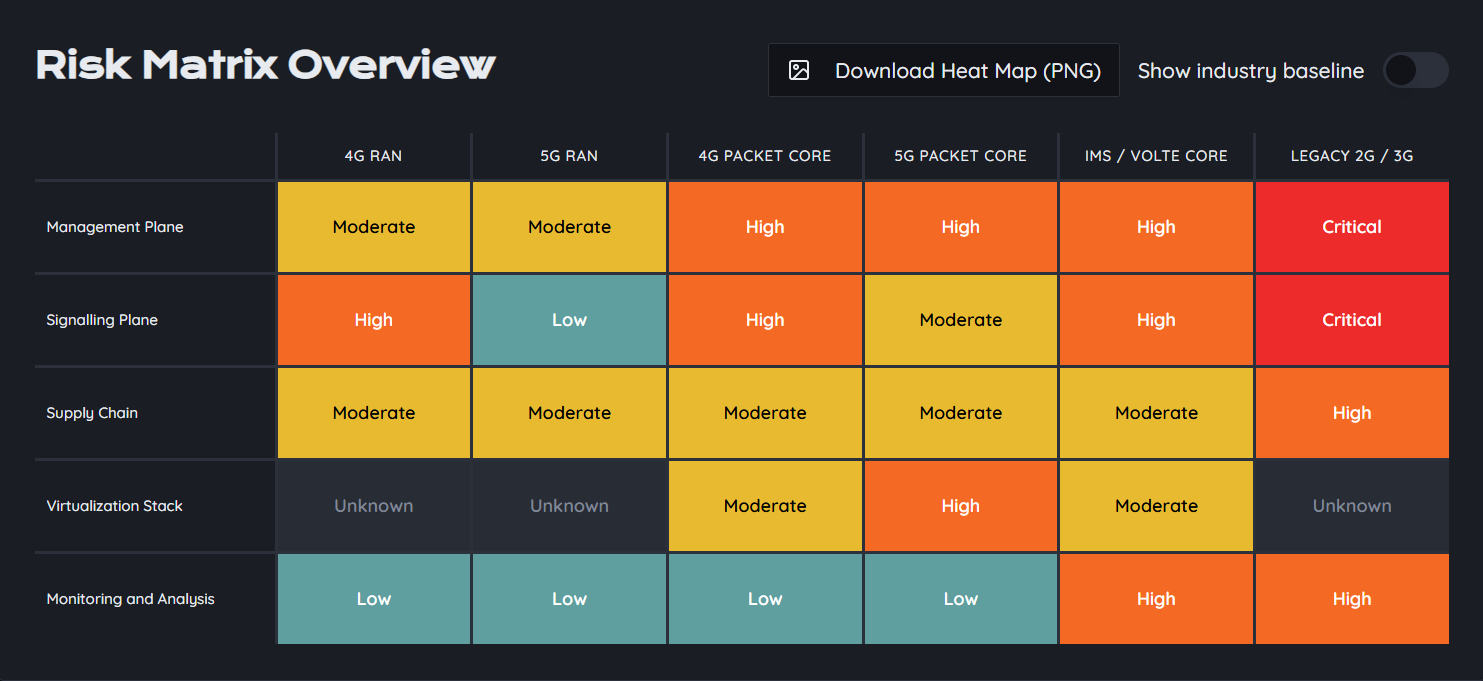
Identify weak components of your systems and networks
Comprehensively identify and understand an organization's attack surface. Reduce the attack surface by eliminating unnecessary assets, services, or configurations that may be vulnerable.


Align with regulator requirements
Assists organizations in complying with relevant cybersecurity regulations and industry standards by ensuring that their attack surface aligns with compliance requirements.
Get verifiable attestation that your infrastructure was not tampered with
Make sure with an in-depth analysis of your protocol and of your infrastructure that no attackers could have exploited a vulnerability to target your subscribers.

Key numbers
2000
Number of unique vulnerabilities identified
0
The percentage of missions where our team did not find a vulnerability
500