As 5G networks expand globally, telecom operators are embracing the revolutionary potential of ultra-fast, low-latency connectivity. However, with these advancements come significant security challenges. Protocols, such as SS7, Diameter, GTP-C, and SIGTRAN, as well as innovations like network slicing and edge computing, create a complex security landscape that telecom providers must navigate to protect their infrastructures from a growing range of cyber threats.
Understanding the Complexities of 5G Security
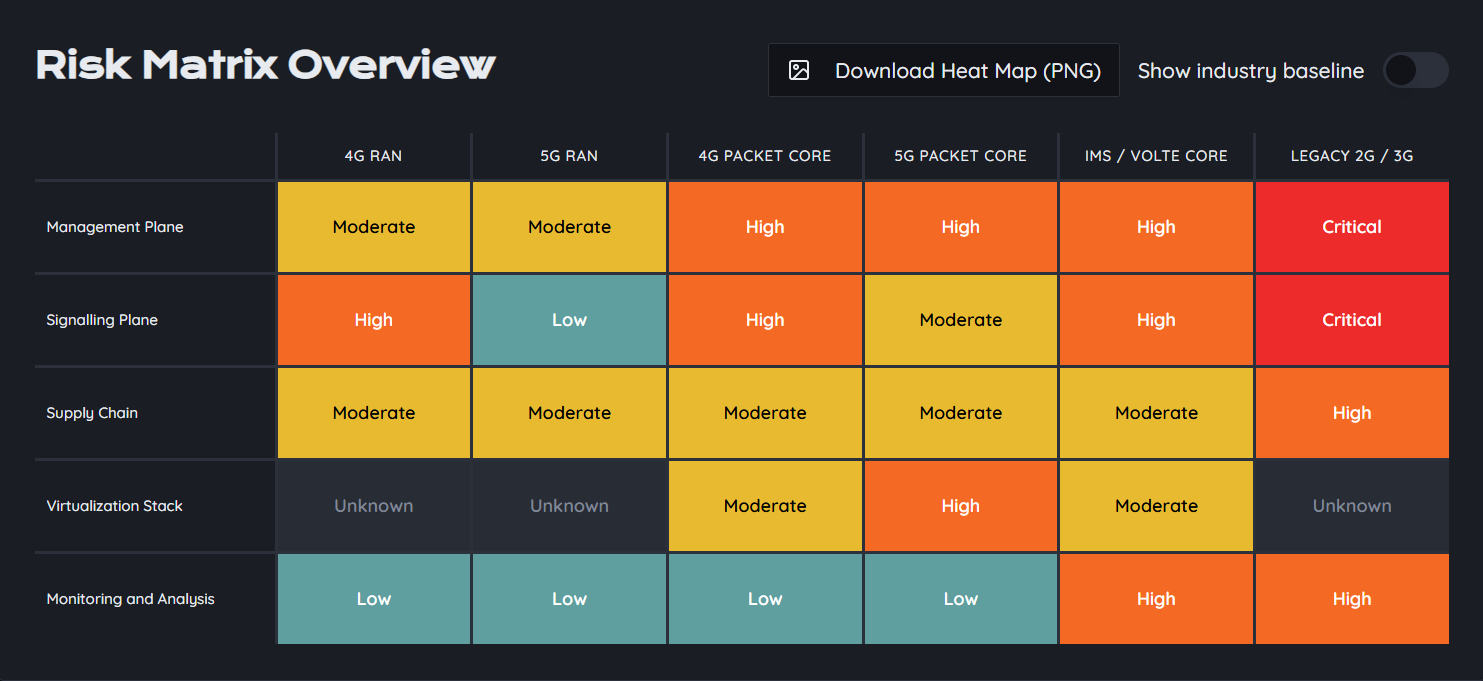
The shift to 5G brings remarkable benefits but also introduces new vulnerabilities. 5G networks are vastly more complex than their predecessors, relying on advanced technologies like virtualized environments and distributed architectures. While these innovations improve efficiency and user experience, they also expand the attack surface, making the networks more susceptible to cyberattacks.
Traditional telecom protocols like SS7 and Diameter remain vital, and their vulnerabilities are often exploited by cybercriminals. These legacy systems were not designed with the scale or complexity of 5G in mind, yet they continue to play a critical role in network operations, leaving telecom operators exposed if not properly secured.
The Role of Key Protocols in 5G Security
- SS7 (Signaling System 7):While SS7 is a foundational protocol in telecom networks, it is also notorious for its security gaps. Attackers can exploit these weaknesses to intercept calls and messages, track users, and launch fraud attacks, such as SIM-swapping. As 5G deployments progress, the risk of these vulnerabilities being used for more sophisticated attacks increases, demanding a more vigilant approach to security.
- Diameter Protocol:Diameter serves as the AAA (authentication, authorization, and accounting) protocol in modern telecom networks, including 5G. However, like SS7, Diameter is vulnerable to attacks that could bypass authentication or manipulate billing and accounting data, leading to data theft or fraud. Network operators must safeguard Diameter implementations with the latest security measures to minimize these risks.
- GTP-C (GPRS Tunneling Protocol Control):GTP-C facilitates communication between network components in mobile networks, including 5G. Attackers targeting GTP-C could execute denial-of-service (DoS) attacks or intercept and manipulate traffic. Given 5G's increasing traffic load, securing GTP-C is paramount to maintaining service integrity.
- SIGTRAN:As a protocol for transporting signaling over IP networks, SIGTRAN connects legacy SS7 systems to newer networks. While it enables the migration to 5G, SIGTRAN's vulnerabilities need attention. Cybercriminals could exploit flaws in SIGTRAN to inject malicious traffic or intercept critical communications.
The Growing Complexity of 5G Networks: Emerging Threats
5G networks present a broader and more intricate attack surface than ever before. New technologies such as network slicing and edge computing increase the opportunities for attackers to exploit vulnerabilities. Network slicing, for example, allows operators to create isolated virtual networks for specific use cases, but this also means that a breach in one slice could potentially compromise others. Edge computing pushes data processing closer to end-users, but securing edge devices is increasingly difficult due to their vast number and variety.
Additionally, telecom operators must account for the growing risks of AI-driven cyberattacks. Automated tools powered by machine learning are being used by adversaries to launch more sophisticated and rapid attacks, far outpacing traditional security defenses.
Securing 5G: Key Measures for Telecom Operators
To protect the integrity of 5G networks, operators must adopt a multi-layered approach to security:
- Zero Trust Architecture: Implementing a Zero Trust model ensures that no entity is trusted by default, whether inside or outside the network. Every transaction and connection must be authenticated, which helps mitigate internal and external threats.
- Encryption and Strong Authentication: Strong encryption is essential for protecting data in transit, particularly in light of the increasing volume of sensitive data transmitted over 5G. Multi-factor authentication (MFA) is a must to prevent unauthorized access to network elements.
- Continuous Monitoring and Threat Detection: AI/ML-based threat detection systems are increasingly important for real-time monitoring. By leveraging machine learning algorithms, telecom operators can spot abnormal behavior and prevent attacks before they cause significant damage.
- Securing Network Slicing and Edge Computing: Since 5G networks rely heavily on network slicing and edge computing, robust security measures must be implemented across all virtual networks and edge devices to ensure data integrity and prevent lateral movement of attacks.
- Comprehensive Security Testing: Regular penetration testing and vulnerability assessments are critical to identifying weaknesses in the network and preventing attacks. Ensuring that all protocols, including SS7, Diameter, and GTP-C, are secure is essential to maintaining a resilient telecom infrastructure.
The Role of P1 Security in 5G Security
P1 Security specializes in securing telecom networks and mobile infrastructures. With our deep expertise in mobile network security, we provide telecom operators with the tools and guidance they need to safeguard their 5G deployments. Our solutions are designed to address the vulnerabilities inherent in legacy protocols like SS7 and Diameter, while also securing new technologies.
Our comprehensive approach includes continuous monitoring, pen-testing, and security consulting, ensuring that telecom operators can keep pace with evolving threats. P1 Security helps operators reduce their attack surface, mitigate risks, and maintain the confidentiality and integrity of their communications networks.
Conclusion
As telecom operators are racing to deploy 5G networks globally, security must be a top priority. The new opportunities brought by 5G technologies come with a range of risks that must be managed proactively. By focusing on securing critical protocols, embracing a Zero Trust security model, and continuously testing for vulnerabilities, telecom providers can minimize their exposure to threats.
P1 Security is committed to helping telecom operators navigate the complexities of 5G security, ensuring their infrastructures remain secure, resilient, and ready to handle the challenges of tomorrow’s connected world.
🔐 Looking for the full picture? Explore the Ultimate Guide to Mobile Network Security — your complete resource on telecom security, from architecture to audits.