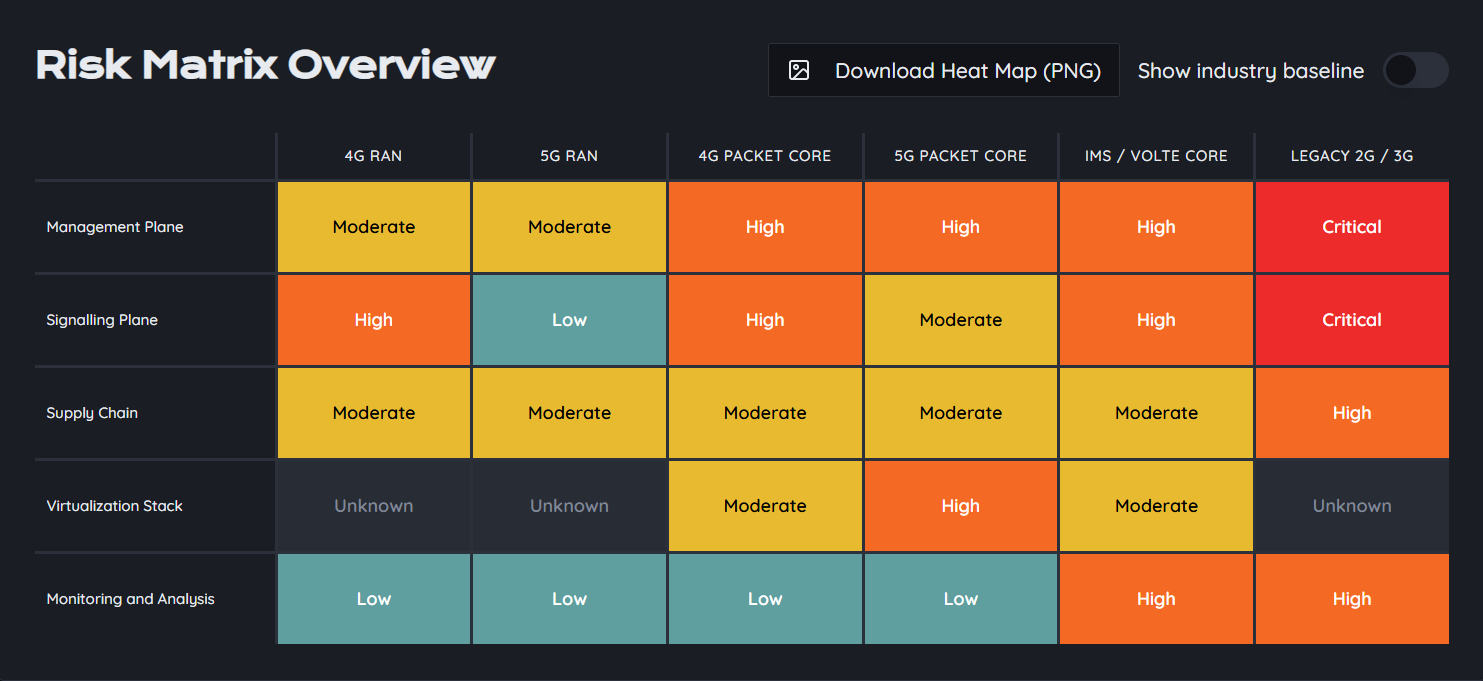
In an increasingly interconnected world, the importance of robust telecom security cannot be overstated. As our reliance on mobile and fixed communication systems grows, so does the necessity to protect these infrastructures from a diverse range of cyber threats. Telecom networks serve as the backbone of global communication, facilitating everything from voice calls to data transmission and Internet of Things (IoT) services. However, they are also prime targets for cybercriminals looking to exploit vulnerabilities.
The Landscape of Telecom Security
The methods, tools, and techniques used to protect communication networks against intrusions and cyberattacks are collectively referred to as telecom security. Telecom operators confront more threats and complexity as they go from 4G to 5G. Security is a primary concern because this shift not only improves connectivity but also increases the attack surface.
Understanding SS7 and Its Vulnerabilities
The Signaling System No. 7 (SS7) protocol is integral to telecommunications, facilitating call setup, routing, and mobile tracking. However, its architecture is fraught with vulnerabilities that attackers can exploit.
- SS7 Protocol Overview: The SS7 protocol stack is crucial for enabling communication between different networks and mobile devices. It handles signaling messages that establish calls and manage other telecommunications functions. Yet, its design lacks sufficient security measures, leaving it susceptible to attacks.
- Types of SS7 Attacks: Cybercriminals can use SS7 vulnerabilities to intercept calls and messages, track users' locations, and impersonate legitimate users. The SS7 attack in 2024 has demonstrated how easily these vulnerabilities can be exploited, leading to severe implications for user privacy and network security.
- Mobile Tracking and SS7: Attackers can leverage SS7 for mobile tracking, allowing them to monitor users without their consent. This form of surveillance poses significant privacy risks and highlights the necessity for stringent security protocols.
- SS7 Encryption: While SS7 lacks built-in encryption, implementing additional encryption layers can help protect sensitive data as it traverses the network, reducing the risks associated with SS7 attacks.
- Common Vulnerabilities: It is essential for telecom providers to comprehend SS7 vulnerabilities. These weaknesses, which can result in successful cyberattacks, include old equipment, incorrect setups, and a lack of monitoring..
Diameter Protocol: The Next Generation of Security
As networks evolve towards 5G, the Diameter protocol becomes increasingly relevant. Designed as a successor to RADIUS, Diameter is essential for authentication, authorization, and accounting (AAA) in telecom systems.
- Diameter in 4G and 5G: The Diameter protocol is integral to managing subscriber data and session management in 4G and 5G networks. It allows for more complex interactions than its predecessor, providing a framework for secure communications.
- Diameter Protocol Vulnerabilities: Like SS7, the Diameter protocol is not immune to attacks. Vulnerabilities can arise from improper implementations, weak authentication methods, or insufficient encryption, necessitating regular audits and updates.
- Diameter and SS7: Understanding the relationship between Diameter and SS7 is crucial. Both protocols serve different functions, but their interactions can introduce new vulnerabilities. For instance, if SS7 is exploited, it could lead to unauthorized access to Diameter-based services.
- Diameter Protocol Attack: Cyber threats targeting the Diameter protocol can undermine its integrity, leading to unauthorized data access and service disruptions. As telecom operators increasingly adopt Diameter in their networks, the focus on securing this protocol must intensify.
P1 Security’s Comprehensive Solutions
At P1 Security, we understand the critical need for telecom security and offer a suite of services designed to help operators and nation-states protect their networks against cybersecurity threats. Our solutions include:
- PTA (P1 Telecom Auditor): A robust auditing tool that assesses the security posture of telecom networks, identifying vulnerabilities and providing actionable insights for remediation, particularly in protocols like SS7, Diameter and GTP-C.
- PTM (P1 Telecom Monitor): This monitoring solution continuously observes network activities, enabling real-time threat detection and response to potential security incidents.
- VKB (P1 Vulnerability Knowledge Base): An extensive database that catalogs vulnerabilities across various telecom protocols, helping organizations stay informed and proactive in their security measures.
- OTP (Online Training Platform): We offer specialized training sessions aimed at educating telecom personnel about the latest security threats and best practices, ensuring they are well-equipped to handle potential challenges.
Securing the Future of Telecom
The need for improved security measures is become more pressing as the telecom environment continues to change. Telecom operators need to be proactive in understanding their networks, putting strong security measures in place, and keeping an eye out for any vulnerabilities due to the increasing sophistication of cyber attacks.
By leveraging P1 Security's innovative solutions and expertise, organizations can not only safeguard their networks but also ensure compliance with regulatory requirements and industry standards. The future of telecom security lies in a collaborative effort to fortify our communication networks against the myriad of threats they face.
For more information on how P1 Security can enhance your telecom security, contact us today. Together, we can build a secure and resilient telecom environment for the future.
🔐 Looking for the full picture? Explore the Ultimate Guide to Mobile Network Security — your complete resource on telecom security, from architecture to audits.