Telecommunication networks have evolved rapidly over the past few decades. With the rise of 4G and 5G technologies, the legacy networks—2G and 3G—are gradually being phased out. This transition is not only a technological shift but also a critical moment for telecom operators, users, and security professionals to reconsider the security implications.
As these older generations of networks are decommissioned, their retirement poses new risks and opportunities for mobile network security. In this article, we’ll explore the reasons behind the phasing out of 2G and 3G, the security risks involved, and how operators can protect their infrastructures as they transition to newer technologies.
Why Are 2G and 3G Networks Being Phased Out?
The move away from 2G and 3G networks is primarily driven by several factors:
1. Technological Advancements
With the advent of 4G and 5G technologies, the need for older network infrastructures has diminished. These newer generations provide faster speeds, lower latency, and improved coverage, making them more suitable for the growing demands of modern telecommunications. Additionally, 4G and 5G technologies support more advanced services, such as IoT (Internet of Things) and high-definition video streaming.
2. Cost Efficiency
Maintaining multiple generations of networks can be costly for telecom operators. Phasing out legacy networks allows operators to focus on modernizing and optimizing their 4G and 5G infrastructures, reducing maintenance and operational costs.
3. Spectrum Efficiency
2G and 3G networks require significant amounts of spectrum that could be better utilized for newer technologies. By reallocating this spectrum to 4G and 5G, telecom operators can improve network capacity and offer more efficient services.
4. End of Support
Many vendors are ceasing support for 2G and 3G technologies, including hardware and software updates. As these networks become increasingly obsolete, it becomes harder to ensure that they remain secure and efficient. This lack of support makes them vulnerable to cyberattacks.
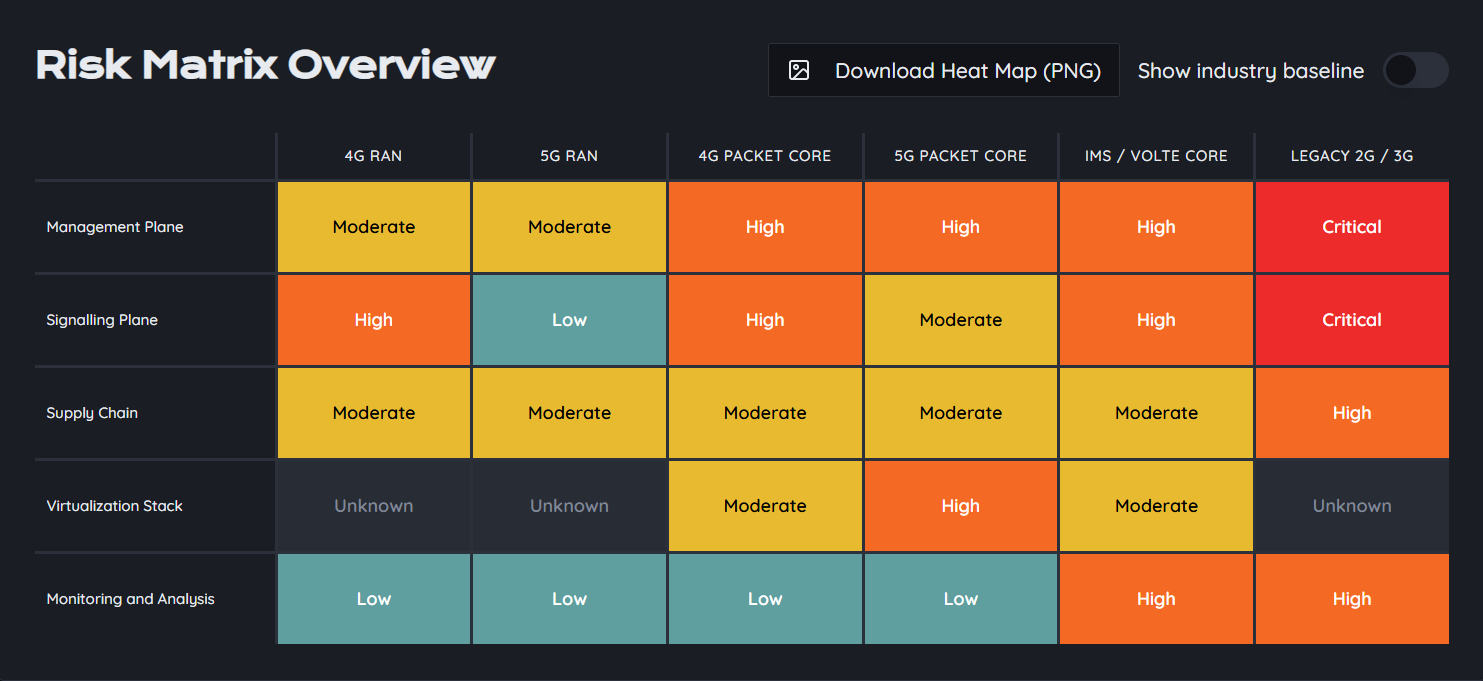
Security Risks Associated with the Phasing Out of 2G and 3G Networks
While the decommissioning of 2G and 3G networks offers many benefits, it also comes with security challenges that need to be addressed:
1. Vulnerabilities in Legacy Systems
2G and 3G networks have long been known to have security weaknesses. For instance, 2G’s lack of encryption makes it susceptible to interception attacks, where cybercriminals can eavesdrop on communications and steal sensitive data. 3G improved security somewhat but still lacks the robust encryption and authentication mechanisms of modern technologies like 4G and 5G. As these networks are decommissioned, they could become even more vulnerable to attacks.
2. Exploitation of Unused Infrastructure
Once 2G and 3G networks are phased out, there may still be infrastructure left behind, creating potential attack vectors. Hackers could exploit these unused systems to launch attacks or gain unauthorized access to operators' infrastructures. Telecom operators must ensure that decommissioned hardware and software are securely deactivated and disposed of.
3. Increased Attack Surface in Transition
As telecom operators transition to 4G and 5G, the infrastructure will likely become more complex, leading to an expanded attack surface. While 4G and 5G offer more advanced security features, such as improved encryption and authentication, they also introduce new threats, including the potential for targeted attacks on new technologies like IoT devices or 5G network slicing.
4. Impact on Subscribers Still Using 2G and 3G Devices
Many users, especially in rural areas or developing regions, still rely on 2G and 3G devices. As these networks are phased out, users may be left with limited access to mobile services. Moreover, these older devices typically lack the security features of newer models, making them more susceptible to cyber threats. The transition period may expose these users to higher risks of security breaches and fraud.
5. Interoperability Issues
As telecom operators begin to phase out legacy networks, there may be periods of overlap, where 2G, 3G, and 4G/5G networks need to coexist. This could result in security gaps, as the older technologies may not seamlessly integrate with newer systems, leaving vulnerabilities open for exploitation.
Steps Telecom Operators Can Take to Secure Their Networks During the Transition
The phasing out of 2G and 3G networks requires careful planning and robust security measures. Here are some steps telecom operators should take to secure their infrastructures during this transition:
1. Decommission Legacy Infrastructure Securely
It’s critical for telecom operators to follow best practices for securely decommissioning 2G and 3G network infrastructure. This includes wiping sensitive data from old hardware, ensuring that outdated systems are properly disconnected from the network, and preventing unauthorized access. Regular audits and vulnerability assessments should be conducted to ensure no security gaps are left open.
2. Upgrade to 4G/5G with Enhanced Security Features
4G and 5G technologies provide stronger encryption, better user authentication, and more advanced security protocols. Telecom operators should prioritize the implementation of these enhanced security features to safeguard their networks and protect against emerging threats. Transitioning to these newer technologies can reduce vulnerabilities and provide a more secure environment for both users and operators.
3. Migrate Users to Newer Devices
Telecom operators should encourage users to upgrade to newer devices that are compatible with 4G and 5G networks. This can help ensure that customers benefit from the enhanced security features of modern mobile technologies. Telecom companies can offer incentives, such as discounts or trade-in programs, to ease the transition.
4. Monitor for Threats During the Transition
During the phase-out process, operators should closely monitor network traffic for signs of malicious activity. This includes monitoring for any unauthorized access attempts, unusual network behaviors, or potential exploits targeting legacy systems. A proactive security approach will help operators detect and mitigate risks early.
5. Educate Customers on Security Risks
Telecom operators should provide educational resources to their customers about the security risks of using outdated devices and networks. Offering advice on upgrading to secure devices and understanding the importance of modern network security will help users protect themselves from potential threats.
6. Plan for IoT Security in 5G Networks
With the rise of 5G, IoT devices will become more prevalent and interconnected. Telecom operators must adopt a security-first approach to IoT integration, ensuring that devices are secure by design, that network slicing is properly configured, and that new vulnerabilities are mitigated through regular testing and security updates.
Global Plans for Phasing Out 2G and 3G Networks
Several countries have announced plans for phasing out 2G and 3G networks in the upcoming years. Here are some key dates:
- United States: Major U.S. operators like AT&T and T-Mobile have already started decommissioning 2G and 3G networks. AT&T completely shut down its 3G network in February 2022, and T-Mobile decommissioned its 2G network and ended 3G service in 2022.
- Germany: Deutsche Telekom, the largest telecom provider in Germany, has announced plans to shut down its 3G network by 2025. This is part of a broader strategy to prioritize 5G development and phase out legacy networks.
- United Kingdom: Vodafone UK will phase out its 3G network by 2023, and many other operators are focusing on 4G and 5G services, signaling the end of 2G/3G networks in the near future.
- France: French telecom operators like Orange and SFR are in the process of phasing out 3G services. Orange plans to shut down its 3G network by 2025, with a strong focus on upgrading to 4G and 5G networks.
- India: Bharti Airtel plans to phase out its 3G network by 2024, with the transition to 4G and 5G services.
- Australia: Telstra is shutting down its 3G network by 2024, while Optus is focusing on 4G and 5G services, signaling the end of 2G/3G networks in the near future.
- South Korea: SK Telecom is planning to phase out 2G by 2025, while it has already focused on expanding 4G and 5G networks across the country.
- Gulf Cooperation Council (GCC) Countries: In the GCC region, the telecom sector is rapidly adopting 5G, and many countries are phasing out older technologies. For example:
- United Arab Emirates: The major telecom operators, Etisalat and du, have already significantly reduced 3G usage, and Etisalat plans to fully decommission 3G by 2025.
- Saudi Arabia: Saudi Telecom Company (STC) and other operators are focused on 4G and 5G, with gradual phasing out of 3G and 2G networks by 2025.
- Italy: Telecom Italia (TIM) plans to phase out its 3G network by 2025, as the company focuses on expanding its 4G and 5G services.
- Spain: Movistar and Vodafone Spain are planning to phase out 3G services by 2024 as part of a broader move towards 4G and 5G.
How P1 Security Can Help
At P1 Security, we specialize in securing telecom networks across all generations, from 2G to 5G. Our expertise in telecom security, including vulnerability assessments, penetration testing, and security audits, helps operators manage the transition from 2G and 3G networks to more secure 4G and 5G environments. By partnering with P1 Security, telecom operators can ensure that their infrastructure remains secure throughout this critical transition.
Our solutions, such as the P1 Telecom Auditor (PTA) and The Vulnerability Knowledge Base (VKB), provide real-time security insights and the tools necessary to manage the security of evolving mobile networks.
Conclusion
The phasing out of 2G and 3G networks marks a significant milestone in the evolution of telecommunications. While this transition presents exciting opportunities for faster and more secure mobile technologies, it also brings new security challenges that must be addressed. By taking proactive steps to secure their infrastructures, educate customers, and transition smoothly to 4G and 5G, telecom operators can ensure a secure future for both their networks and users.
At P1 Security, we are committed to helping telecom operators navigate these changes and secure their mobile networks against evolving threats.
🔐 Looking for the full picture? Explore the Ultimate Guide to Mobile Network Security — your complete resource on telecom security, from architecture to audits.